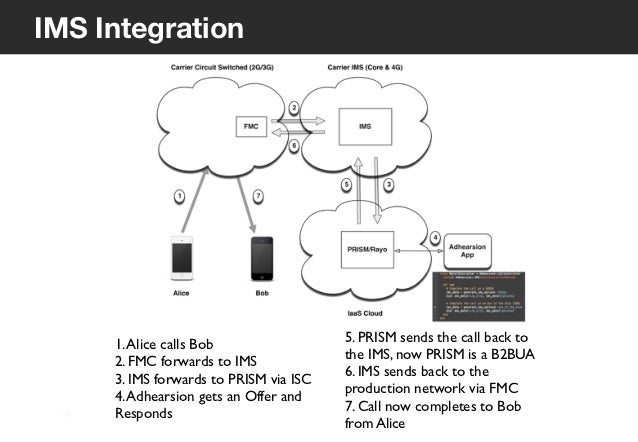
Cisco ISE AD integration. ISE node must be added to domain as a host (computer) ISE node need privileges to read LDAP / AD directory (needed for authentication) Need to have user with privileges to add machined to domain, there are specific cases when ISE node is added to AD Offline.
Actually when you do AD integration - You are doing integration with FMC so FMC should be reachable always, and for this specific error i cannot comment but i can recommend you to run latest released software for FMC and FTD both device. IF you are using 6.2.3 - it is better to go with 6.2.3.13 please check release note before doing update. The purpose of this guide is to provide guidelines on how to integrate Mideye two-factor authentication with Cisco AnyConnect using Cisco FMC. Prerequisites & general issues. A Mideye Server (any release). If there is a firewall between the Cisco FMC and the Mideye Server, it must be open for two-way RADIUS traffic (UDP, standard port 1812). Fresenius Medical Care North America welcomes your inquiries. For technical support and product training, call (800) 227-2572 toll-free 24/7. The FMC has had pxGrid integration with ISE for a while, but version 6.2 added an even better integration, with the ability to use the TrustSec data independent of user identities. The FMC can use context information provided by pxGrid, such as endpoint profiles, TrustSec tags, and both passive and active user identities.
Introduction
This document describes the configuration process for integration of the Identity Services Engine (ISE) pxGrid version 2.4 and Firepower Management Center (FMC) version 6.2.3.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- ISE 2.4
- FMC 6.2.3
- Active Directory/Lightweight Directory Access Protocol (LDAP)
Components Used
The information in this document is based on these software and hardware versions:
- Standalone ISE 2.4
- FMCv 6.2.3
- Active Directory 2012R2
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Configure ISE
Step 1. Enable pxGrid Services
- Log into the ISE Admin GUI, navigate to Administration > Deployment.
2. Select the ISE node to be used for pxGrid persona as shown in the image.
3. Enable pxGrid service and click Save as shown in the image.
4. Verify that the pxGrid services are running from the CLI.
Note: It might take up to 5 minutes for the pxGrid services to fully start and determine High Availability (HA) state if more than one pxGrid node is in use.
5. SSH into the ISE pxGrid node CLI and check the application status.
6. Access the ISE Admin GUI and verify that the services are online and working. Navigate to Administration > pxGrid Services.
7. At the bottom of the page, ISE should display Connected to pxGrid as shown in the image.
Step 2. Configure ISE to Approve all pxGrid Certificate-Based Accounts
1. Navigate to Administration > pxGrid Services > Settings.
2. Check the box: 'Automatically approve new certificate-based accounts' and click Save as shown in the image.
Note: The administrator should manually approve the FMC connection to ISE if this option is not enabled.
Step 3. Export ISE MNT Admin Certificate and pxGrid CA Certificates
1. Navigate to Administration > Certificates > System Certificates.
2. Expand the Primary Monitoring (MNT) node if not enabled on the Primary Administration node.
3. Select the certificate with the Used-By 'Admin' field.
Note: This guide uses the default ISE Self-Signed Certificate for Admin usage. If you use a Certificate Authority (CA) signed Admin Certificate you need to export the Root CA that signed the Admin certificate on the ISE MNT node.
4. Click Export.
5. Choose the option to Export Certificate and Private Key.
6. Set an encryption key.
7. Export and Save the file as shown in the image.
9. Return to the ISE System Certificates screen.
10. Determine the Issued By field on the certificate with the 'pxGrid' usage in the Used By column.
Note: In older versions of ISE, this was a self-signed certificate, but from 2.2 onwards this certificate is issued by the Internal ISE CA Chain by default.
11. Select the Certificate and click View as shown in the image.
12. Determine the top level (Root) certificate. In this case it is 'Certificate Services Root CA - tim24adm'.
13. Close the certificate view window as shown in the image.
14. Expand the ISE Certificate Authority Menu.
15. Select Certificate Authority Certificates.
16. Select the Root Certificate that was identified and click Export. Then save the pxGrid Root CA certificate as shown in the image.
Configure FMC
Step 4. Add a new realm to FMC
- Access the FMC GUI and navigate to System > Integration > Realms.
- Click on New Realm as shown in the image.
3. Fill out the form and click the Test Active Directory (AD) Join button.
Note: The AD Join Username should be in User Principal Name (UPN) format or the test fails (user@domain.com).
4. If the Test AD Join is successful, click OK.
5. Click on the Directory tab and then click Add directory as shown in the image.
6. Configure IP/Hostname and Test Connection.
Note: If the Test fails, verify the credentials on the Realm Configuration tab.
7. Click OK.
8. Click the User Download tab as shown in the image.
9. If not already selected, enable user and group download
10. Click Download Now
11. Once the list populates, add desired groups and select Add to Include.
12. Save the Realm Configuration.
13. Enable the Realm State as shown in the image.
Step 5. Generate FMC CA Certificate
1. Navigate to Objects > Object Management > Internal CAs as shown in the image.
2. Click Generate CA.
3. Fill out the form and click Generate self-signed CA as shown in the image.
4. Once generation completes, click on the pencil to the right of the generated CA Certificate as shown in the image.
5. Click Download.
6. Configure and confirm the encryption password and click OK.
7. Save the Public-Key Cryptography Standards (PKCS) p12 file to your local file system.
Step 6. Extract the Certificate and Private Key from the Generated Certificate with the Use of OpenSSL
This might be done either on root of the FMC, or on any client capable of running OpenSSL commands. This example uses a standard Linux shell.
1. Use openssl in order to extract the certficate (CER) and private key (PVK) from the p12 file.
2. Extract the CER file then configure the certificate export key from the cert generation on FMC.
3. Extract the PVK file, configure the certificate export key, then set a new PEM pass phrase and confirm.
4. You will need this PEM phrase in the next step.
Step 7. Install certificate into FMC
1. Navigate to Objects > Object Management > PKI > Internal Certs.
2. Click Add Internal Cert as shown in the image.
3. Configure a name for the Internal Certificate.
4. Browse to the location of the CER file and select it. Once the Certificate Data populates, select the second.
5. Browse Option and select the PVK file.
6. Delete any leading 'Bag attributes' and any trailing values in the PVK section. The PVK should begin with -----BEGIN ENCRYPTED PRIVATE KEY----- and end with -----END ENCRYPTED PRIVATE KEY-----.
Note: You will not be able to click OK if the PVK text has any characters outside of the leading and trailing hyphens.
7. Check the Encrypted box and configure the password created when the PVK was exported in Step 6.
8. Click OK.
Step 8. Import the FMC Certificate into ISE
1. Access the ISE GUI and navigate to Administration > System > Certificates > Trusted Certificates.
2. Click Import.
3. Click Choose File and select the FMC CER file from your local system.
Optional: Configure a Friendly Name.
4. Check Trust for authentication within ISE.
Optional: Configure a Description.
5. Click Submit as shown in the image.
Step 9. Configure pxGrid Connection on FMC
1. Navigate to System > Integration > Identity Sources as shown in the image.
2. Click ISE.
3. Configure the IP address or hostname of the ISE pxGrid node.
4. Select the + to the right of pxGrid Server CA.
5. Name the Server CA file and then browse to the pxGrid Root Signing CA collected in Step 3. and click Save.
6. Select the + to the right of MNT Server CA.
7. Name the Server CA file and then browse to the Admin certificate collected in Step 3. and click Save.
8. Select the FMC CER file from the dropdown list.
9. Click Test.
10. If the test is successful, click on OK, then Save at the top right of the screen.
Note: When you run 2 ISE pxGrid nodes, it is normal for one host to show Success and one to show Failure since pxGrid only runs actively on one ISE node at a time. It depends on the configuration whether which Primary host might display Failure and Secondary host might display Success. This is all dependent on which node in ISE is the active pxGrid node.
Verify
Verification in ISE
1. Open the ISE GUI and navigate to Administration > pxGrid Services.
If all was successful, there should be two firepower connections listed in the client list. One for the actual FMC (iseagent-hostname-33bytes), and one for the test device that was used when you clicked the Test button in FMC (firesightisetest-hostname-33bytes).
The iseagent-firepower connection should display 6 subs and appear online.
The firesightisetest-firepower connection should display 0 subs and appear offline.
Expanded view of the iseagent-firepower client should display the six subscriptions as shown in the image.
Note: Due to CSCvo75376there is a hostname limitation and Bulk Download fails. The test button on the FMC displays a connectivity failure. This affects 2.3p6, 2.4p6, and 2.6. The current recommendation is to run 2.3 patch 5 or 2.4 patch 5 until an official patch is released.
Verification in FMC
1. Open the FMC GUI and navigate to Analysis > Users > Active Sessions.
Any Active Sessions published via the Session Directory capability in ISE should be displayed in the Active Sessions table on FMC.
From the FMC CLI sudo mode, the 'adi_cli session' should display the user session information sent from ISE to FMC.
Troubleshoot
There is currently no specific troubleshooting information available for this configuration.
Introduction
This document describes the configuration of Captive portal authentication (Active Authentication) and Single-Sign-On (Passive Authentication).
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Sourcefire Firepower devices
- Virtual device models
- Light Weight Directory Service (LDAP)
- Firepower UserAgent
Components Used
The information in this document is based on these software and hardware versions:
- Firepower Management Center (FMC) version 6.0.0 and above
- Firepower sensor version 6.0.0 and above
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Background Information
Captive Portal Authentication or Active Authentication prompts a login page and user credentials are required for a host to get the internet access.
Single-Sign-On or Passive Authentication provides seamless authentication to a user for network resources and internet access without entering user credential multiple times. The Single-Sign-on authentication can be achieved either by Firepower user agent or NTLM browser authentication.
Note: For Captive Portal Authentication, appliance must be in routed mode.
Configure
Step 1. Configure the Firepower User Agent for Single-Sign-On
This article explains how to configure Firepower User Agent in a Windows machine:
Step 2. Integrate the Firepower Management Center (FMC) with User Agent
Log in to Firepower Management Center, navigate to System > Integration > Identity Sources. Clickthe New Agent option. Configure the IP address of User Agent system & click the Add button.
Click the Save Autocad 2015 product key serial number. button to save the changes.
Step 3. Integrate Firepower with Active Directory
Step 3.1 Create the Realm
Fmc Ad Integration Manager
Log in to the FMC, navigate to System > Integration > Realm. Clickthe Add New Realm option.
Name & Description: Give a name/description to uniquely identify realm.
Type: AD
AD Primary Domain: Domain name of Active Directory
Directory Username:
Directory Password:
Base DN: Domain or Specific OU DN from where the system will start a search in LDAP database.
Group DN: group DN
Group Attribute: Member
This article helps you to figure out the Base DN and Group DN values.
Step 3.2 Add the Directory Server
Click the Add button in order to navigate to next step and thereafter Click the Add directory option.
Hostname/IP Address: configure the IP address/hostname of the AD server.
Port: 389 (Active Directory LDAP port number )
Encryption/SSL Certificate: (optional) To encrypt the connection between FMC & AD server , refer to the
article: Verification of Authentication Object on FireSIGHT System for Microsoft AD Authentication Over SSL/TLS
Click the Test button in order to verify if FMC is able to connect to the AD server.
Step 3.3 Modify the Realm Configuration
Navigate to Realm Configuration in order to verify integration configuration of AD server and you can modify the AD configuration.
Step 3.4 Download User database
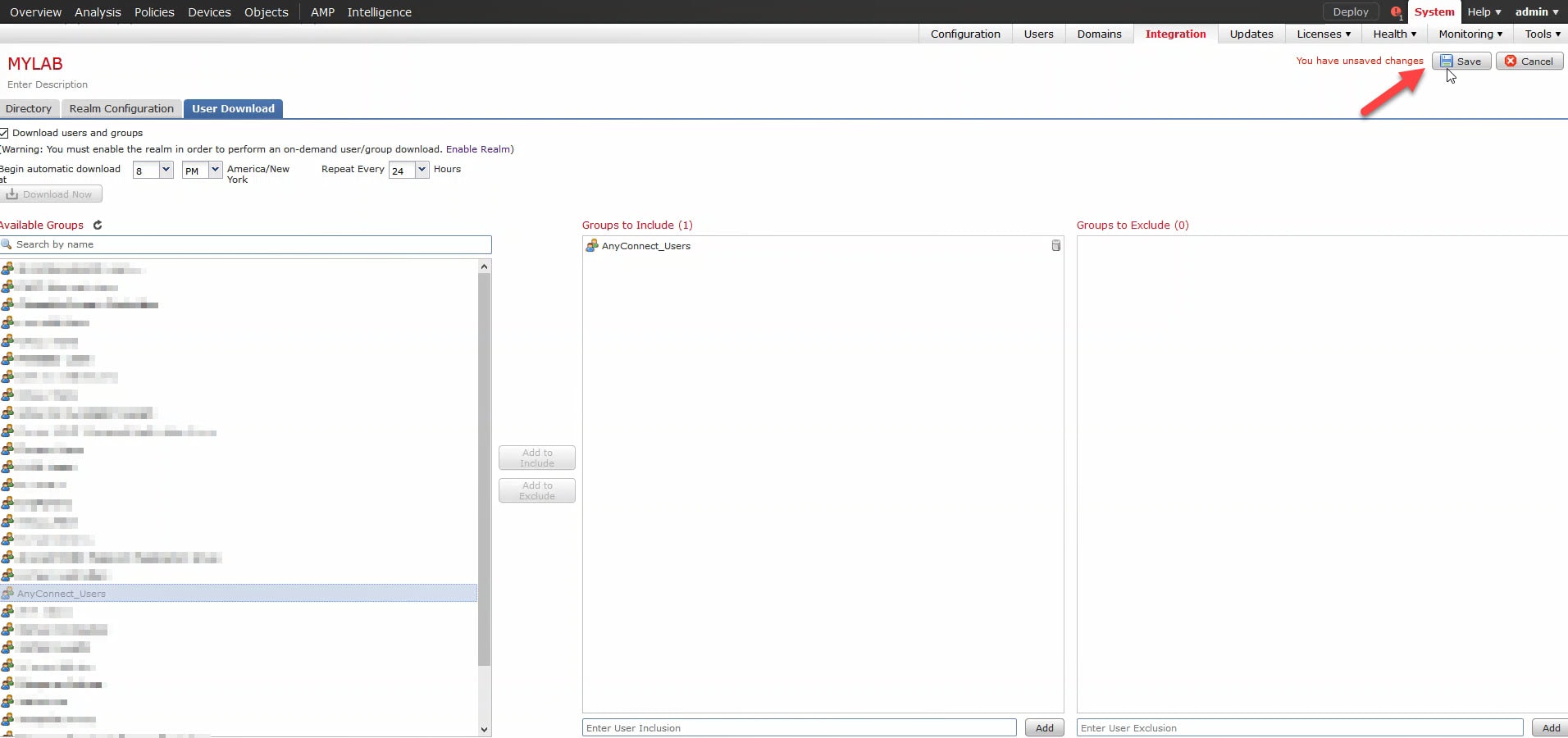
Navigate to User Download option to fetch the user database from the AD server.
Enable the check box to download Download users and groups and define the time interval about how frequently FMC contacts AD to download user database.
Select the group and put it into the Include option for which you want to configure the authentication.
As shown in the image, enable the AD state:
Step 4. Configure the Identity Policy
An identity policy performs user authentication. If the user does not authenticate, access to network resources is refused. This enforces Role-Based Access Control (RBAC) to your organization's network and resources.
Step 4.1 Captive portal (Active Authentication)Active Authentication asks for username/password at the browser to identify a user identity for allowing any connection. Browser authenticates user either by presenting authentication page or authenticates silently with NTLM authentication. NTLM uses the web browser to send and receive authentication information. Active Authentication uses various types to verify the identity of the user. Different types of Authentication are:
- HTTP Basic: In this method, the browser prompts for user credentials.
- NTLM: NTLM uses windows workstation credentials and negotiates it with Active directory using a web browser. You need to enable the NTLM authentication in the browser. User Authentication happens transparently without prompting credentials. It provides a single sign-on experience for users.
- HTTP Negotiate:In this type, the system tries to authenticate using NTLM, if it fails then the sensor will use HTTP Basic authentication type as a fallback method and will prompt a dialog box for user credentials.
- HTTP Response page: This is similar to HTTP basic type, however, here user is prompted to fill the authentication in an HTML form which can be customized.
Each browser has a specific way to enable the NTLM authentication and hence they follow browser guidelines in order to enable the NTLM authentication.
To securely share the credential with the routed sensor, you need to install either self-signed server certificate or publicly-signed server certificate in the identity policy.

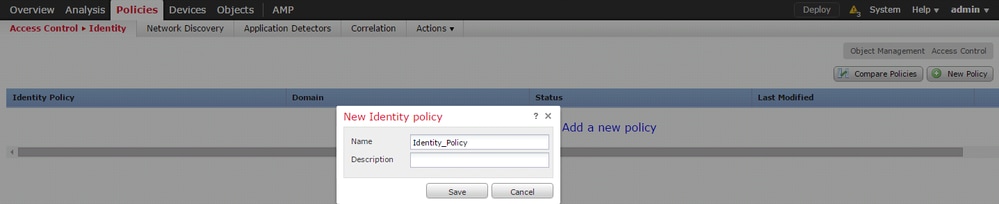
Navigate to Policies > Access Control > Identity. Click the Add Policy & give a name to policy and save it.
Navigate to Active Authentication tab & in the Server Certificate option, click the icon (+) and upload the certificate & private key which you generated in the previous step using openSSL.
Now click the Add rule button & give a name to the Rule & choose the action as Active Authentication. Define the source/destination zone, source/destination network for which you want to enable the user authentication.
Select the Realm, which you have configured in the previous step and authentication type that best suits your environment.
ASA configuration for Captive Portal
For ASA Firepower module, Configure these commands on the ASA in order to configure the captive portal.
Ensure that the server port, TCP 1055 is configured in the port option of Identity policy's Active Authentication tab.
In order to verify the active rules and their hit counts, run following command.
Note: Captive portal command is available in ASA version 9.5(2) and later.
Step 4.2 Single-Sign-On (Passive Authentication)In passive authentication, when a domain user logins and is able to authenticate the AD, the Firepower User Agent polls the User-IP mapping details from the security logs of AD and shares this information with Firepower Management Center (FMC). FMC sends these details to the sensor in order to enforce the access control.
Click the Add rule button & give a name to the Rule & choose the Action as Passive Authentication. Define the source/destination zone, source/destination network for which you want to enable the user authentication.
Select the Realm which you have configured in the previous step and authentication type which best suites your environment, as shown in this image.
Here you can choose fall back method as Active authentication if passive authentication cannot identify the user identity.
Step 5. Configure the Access Control Policy
Navigate to Policies > Access Control > Create/Edit a Policy.
Click the Identity Policy (left-hand side upper corner), choose the Identify Policy that you have configured in the previous step and click the OK button, as shown in this image.
Click the Add rule button to add a new rule, navigate to Users and select the users for which access control rule will enforce, as shown in this image. Click the OK button and click Save button in order to save the changes.
Step 6. Deploy the Access Control Policy
Navigate to Deploy option, choose the Device and click the Deploy option to push the configuration change to the sensor. Monitor the Deployment of policy from the Message Center Icon (icon between Deploy and System option) option and ensure that policy must apply successfully, as shown in this image.
Step 7. Monitor user events & Connections events
Currently active user sessions are available in the Analysis > Users > Users section.
User Activity monitoring helps to figure out which user has associated with which IP address and how is user detected by the system either by active or passive authentication. Analysis > Users > User Activity
Navigate to Analysis > Connections > Events, to monitor the type of traffic being used by the user.
Verify and Troubleshoot
Navigate to Analysis > Users in orderto verify the User authentication/Authentication type/User-IP mapping/access rule associated with the traffic flow.
Verify Connectivity between FMC and User Agent (Passive Authentication)
Firepower Management Center (FMC ) uses TCP port 3306, in order to receive user activity log data from the User Agent.
In order to verify the FMC service status, use this command in the FMC.
Run packet capture on the FMC in order to verify connectivity with the User Agent.
Navigate to Analysis > Users > User Activity in order to verify whether the FMC is receiving user login details from the User Agent. Menace punk singles collection.
Verify Connectivity between FMC and Active Directory
FMC uses TCP port 389 in order to retrieve User Database from the Active directory.
Run packet capture on the FMC to verify connectivity with the Active Directory.

Ensure that the user credential used in FMC Realm configuration has sufficient privilege to fetch the AD's User database.
Verify the FMC realm configuration, and ensure that the users/groups are downloaded and user session timeout is configured correctly.
Fmc Ad Integration System
Navigate to Message Center > Tasks and ensure that the task users/groups download completes successfully , as shown in this image.
Verify Connectivity between Firepower Sensor and End system (Active Authentication)
For active authentication, ensure that the certificate and port are configured correctly in FMC Identity policy.By default, Firepower sensor listens on TCP port 885 for active authentication.
Verify Policy configuration & Policy Deployment
Ensure that the Realm, Authentication type, User agent and Action fields are configured correctly in Identity Policy.
Ensure that the Identity policy is correctly associated with the Access Control policy.
Navigate to Message Center > Tasks and ensure that the Policy Deployment completes successfully.
Fmc Ad Integration
Analyse the Events logs
Cisco Fmc Ad Integration
Connection and the User Activity events can be used to diagnose whether the user login is successful or not.These events
can also verify which Access Control rule is getting applied on the flow.
Name & Description: Give a name/description to uniquely identify realm.
Type: AD
AD Primary Domain: Domain name of Active Directory
Directory Username:
Directory Password:
Base DN: Domain or Specific OU DN from where the system will start a search in LDAP database.
Group DN: group DN
Group Attribute: Member
This article helps you to figure out the Base DN and Group DN values.
Step 3.2 Add the Directory Server
Click the Add button in order to navigate to next step and thereafter Click the Add directory option.
Hostname/IP Address: configure the IP address/hostname of the AD server.
Port: 389 (Active Directory LDAP port number )
Encryption/SSL Certificate: (optional) To encrypt the connection between FMC & AD server , refer to the
article: Verification of Authentication Object on FireSIGHT System for Microsoft AD Authentication Over SSL/TLS
Click the Test button in order to verify if FMC is able to connect to the AD server.
Step 3.3 Modify the Realm Configuration
Navigate to Realm Configuration in order to verify integration configuration of AD server and you can modify the AD configuration.
Step 3.4 Download User database
Navigate to User Download option to fetch the user database from the AD server.
Enable the check box to download Download users and groups and define the time interval about how frequently FMC contacts AD to download user database.
Select the group and put it into the Include option for which you want to configure the authentication.
As shown in the image, enable the AD state:
Step 4. Configure the Identity Policy
An identity policy performs user authentication. If the user does not authenticate, access to network resources is refused. This enforces Role-Based Access Control (RBAC) to your organization's network and resources.
Step 4.1 Captive portal (Active Authentication)Active Authentication asks for username/password at the browser to identify a user identity for allowing any connection. Browser authenticates user either by presenting authentication page or authenticates silently with NTLM authentication. NTLM uses the web browser to send and receive authentication information. Active Authentication uses various types to verify the identity of the user. Different types of Authentication are:
- HTTP Basic: In this method, the browser prompts for user credentials.
- NTLM: NTLM uses windows workstation credentials and negotiates it with Active directory using a web browser. You need to enable the NTLM authentication in the browser. User Authentication happens transparently without prompting credentials. It provides a single sign-on experience for users.
- HTTP Negotiate:In this type, the system tries to authenticate using NTLM, if it fails then the sensor will use HTTP Basic authentication type as a fallback method and will prompt a dialog box for user credentials.
- HTTP Response page: This is similar to HTTP basic type, however, here user is prompted to fill the authentication in an HTML form which can be customized.
Each browser has a specific way to enable the NTLM authentication and hence they follow browser guidelines in order to enable the NTLM authentication.
To securely share the credential with the routed sensor, you need to install either self-signed server certificate or publicly-signed server certificate in the identity policy.
Navigate to Policies > Access Control > Identity. Click the Add Policy & give a name to policy and save it.
Navigate to Active Authentication tab & in the Server Certificate option, click the icon (+) and upload the certificate & private key which you generated in the previous step using openSSL.
Now click the Add rule button & give a name to the Rule & choose the action as Active Authentication. Define the source/destination zone, source/destination network for which you want to enable the user authentication.
Select the Realm, which you have configured in the previous step and authentication type that best suits your environment.
ASA configuration for Captive Portal
For ASA Firepower module, Configure these commands on the ASA in order to configure the captive portal.
Ensure that the server port, TCP 1055 is configured in the port option of Identity policy's Active Authentication tab.
In order to verify the active rules and their hit counts, run following command.
Note: Captive portal command is available in ASA version 9.5(2) and later.
Step 4.2 Single-Sign-On (Passive Authentication)In passive authentication, when a domain user logins and is able to authenticate the AD, the Firepower User Agent polls the User-IP mapping details from the security logs of AD and shares this information with Firepower Management Center (FMC). FMC sends these details to the sensor in order to enforce the access control.
Click the Add rule button & give a name to the Rule & choose the Action as Passive Authentication. Define the source/destination zone, source/destination network for which you want to enable the user authentication.
Select the Realm which you have configured in the previous step and authentication type which best suites your environment, as shown in this image.
Here you can choose fall back method as Active authentication if passive authentication cannot identify the user identity.
Step 5. Configure the Access Control Policy
Navigate to Policies > Access Control > Create/Edit a Policy.
Click the Identity Policy (left-hand side upper corner), choose the Identify Policy that you have configured in the previous step and click the OK button, as shown in this image.
Click the Add rule button to add a new rule, navigate to Users and select the users for which access control rule will enforce, as shown in this image. Click the OK button and click Save button in order to save the changes.
Step 6. Deploy the Access Control Policy
Navigate to Deploy option, choose the Device and click the Deploy option to push the configuration change to the sensor. Monitor the Deployment of policy from the Message Center Icon (icon between Deploy and System option) option and ensure that policy must apply successfully, as shown in this image.
Step 7. Monitor user events & Connections events
Currently active user sessions are available in the Analysis > Users > Users section.
User Activity monitoring helps to figure out which user has associated with which IP address and how is user detected by the system either by active or passive authentication. Analysis > Users > User Activity
Navigate to Analysis > Connections > Events, to monitor the type of traffic being used by the user.
Verify and Troubleshoot
Navigate to Analysis > Users in orderto verify the User authentication/Authentication type/User-IP mapping/access rule associated with the traffic flow.
Verify Connectivity between FMC and User Agent (Passive Authentication)
Firepower Management Center (FMC ) uses TCP port 3306, in order to receive user activity log data from the User Agent.
In order to verify the FMC service status, use this command in the FMC.
Run packet capture on the FMC in order to verify connectivity with the User Agent.
Navigate to Analysis > Users > User Activity in order to verify whether the FMC is receiving user login details from the User Agent. Menace punk singles collection.
Verify Connectivity between FMC and Active Directory
FMC uses TCP port 389 in order to retrieve User Database from the Active directory.
Run packet capture on the FMC to verify connectivity with the Active Directory.
Ensure that the user credential used in FMC Realm configuration has sufficient privilege to fetch the AD's User database.
Verify the FMC realm configuration, and ensure that the users/groups are downloaded and user session timeout is configured correctly.
Fmc Ad Integration System
Navigate to Message Center > Tasks and ensure that the task users/groups download completes successfully , as shown in this image.
Verify Connectivity between Firepower Sensor and End system (Active Authentication)
For active authentication, ensure that the certificate and port are configured correctly in FMC Identity policy.By default, Firepower sensor listens on TCP port 885 for active authentication.
Verify Policy configuration & Policy Deployment
Ensure that the Realm, Authentication type, User agent and Action fields are configured correctly in Identity Policy.
Ensure that the Identity policy is correctly associated with the Access Control policy.
Navigate to Message Center > Tasks and ensure that the Policy Deployment completes successfully.
Fmc Ad Integration
Analyse the Events logs
Cisco Fmc Ad Integration
Connection and the User Activity events can be used to diagnose whether the user login is successful or not.These events
can also verify which Access Control rule is getting applied on the flow.
Navigate to Analysis > User to check the user events logs.
Navigate to Analysis > Connection Events to check the connection events.
